Returning to the Screen of the Crime

What you need to know and do to protect your cyber supply chain.
Your IT network is a thing of beauty. It enables, advises, analyzes, records, tracks, and connects. It even does Windows. To criminals, however, your network is a safe waiting to be cracked.
The Cyber Supply Chain: Assessing Your Risk
DO’s and DON’Ts of Cyber Security
“Cyber crime costs the global economy more than $400 billion each year, and those costs will continue to grow,” reports PricewaterhouseCoopers. And, 2014 saw nearly 80,000 suspicious security incidents, according to Verizon Enterprise Services. Of these, more than 2,000 were confirmed data breaches.
“Hardly a day goes by without a major company reporting an attempted breach of its systems,” writes Chris Blackhurst in the London Evening Standard. He invokes the IRA’s response to its failed attempt at assassinating Margaret Thatcher: “Today we were unlucky, but we only have to be lucky once. You’ll have to be lucky always.”
A few notable data breach victims include large companies such as Sony, The UPS Store, Anthem, Home Depot, T-Mobile, Citroen, and Target. But cyber burglars break into smaller enterprises, too. For example, criminals recently uncorked customers’ personal data at several California wineries.
The bad guys find a vulnerability—an exploitable software, system, defense, or human flaw. The same way street burglars check windows and doors to find an unlocked, easy entrance, cyber burglars use malware to poke around for a weakness until it finds an easy-to-penetrate network—and gains access.
“Access to a system does not imply that criminals can log in,” explains Gregory D. Tomczyk, director of global service strategy and design for supply chain management company UTi Worldwide. “Access is being able to exploit a weakness or vulnerability to execute a criminal’s intent.”
Hackers on a mission can find and exploit the flaw by planting a worm, a virus, or some form of malware. Don’t overlook someone physically inserting an infected USB stick into a network-connected computer, or an employee opening an email phishing link that may introduce malware.
Stealing More Than Just Data
What data are criminals hijacking? Customer and personnel records offering a bonanza of exploitable personal information: credit card numbers; login information (ID and password); Social Security numbers; passport and driver’s license numbers; and birthdates.
But wait, there’s more. They are also hijacking companies’ proprietary information: correspondence, contracts, intellectual property, customer lists, vendor prices, warehouse CCTV videos, and trade secrets. The enemies are global. Motives range from theft to extortion to competitive spying to doing it just for fun.
Don’t think of customer information as just data. That’s so impersonal. Instead, think of each record as a lawsuit and an angry ex-customer. It’s the kind of thing that keeps IT security professionals up at night.
The supply chain was Ground Zero for both the Target and Home Depot break-in attacks, said Dr. Sandor Boyson research professor and co-director of the Supply Chain Management Center at the University of Maryland’s Robert H. Smith School of Business, in a Washington Post article.
And that is the scary truth for supply chain professionals. The vulnerability might not be in your internal network. One or more of your suppliers or carriers might be lax on security. If your networks are connected, as they probably are, you are out of luck. About 70 percent of malware that successfully penetrates one system migrates to a connected system, often in less than two hours, according to Verizon.
The T-Mobile thieves broke in through Experian, which processes applications for the communications company. Target became a bulls-eye because cyber thieves discovered a vulnerability at one of its third-party vendors, a Pennsylvania-based heating and air conditioning contractor. Burglars ransacked Citroen after gaining entry through a third-party vendor that offered Citroen-branded items.
Add to this the Internet of Things (IoT), where machines talk to machines. Refrigerators order food from a delivery service; smart teakettles turn themselves on; warehouses tell the factory to make more widgets. The IoT adds more data, more sources of data, and more leaky networks to the universe.
The IoT poses a particular threat to logistics and transportation, especially because hackers are not always looking to get in, snatch, and go, says Jeffrey Luft, global practice leader for Verizon Enterprise Solutions’ transportation and distribution verticals.
Hackers might be “looking to take a criminal action down the road,” Luft adds. “That would include things like knowing the inventory location of either a distribution center or retail store; or knowing the inbound cargo on containers coming into the West Coast ports and planning criminal activity around that.”
“The IoT will be largely useless unless it is an Internet of Secure Things,” writes John Villasenor, nonresident senior fellow, governance studies, Center for Technology Innovation in Forbes.
“Suddenly, there’s a big light shining on supply chain information, where there might have been a dim candle looking at it from a protection and security perspective in the past,” says Harold B. Friedman, senior vice president of global corporate development for Data2Logistics, a supply chain finance third-party logistics provider.
The good news is that more robust defensive tools are now available.
“Firewalls are getting bigger and better,” says Joan Ross, managing principal with Verizon Enterprise Solutions’ cybersecurity practice. “Intrusion detection is getting more sensitive, and finely tuned.”
Only 10 of 2014’s more than 7 million exploited vulnerabilities accounted for 97 percent of the year’s incidents, according to Verizon. Most vulnerabilities dated back to 2007, and could have been sidestepped with an available patch.
The better news is that protection is not as much about the latest technology as it is about how you think, prepare, and act.
“There are three phases of attack,” said Ellen Richey, chief enterprise risk officer for Visa Inc., at the Washington Post’s 2015 Cybersecurity Summit. “First is the entry point; second is the theft or destruction therein, third is the monetization of the data.
“The entry point is generally not at all sophisticated,” she added. “Thieves gain access through simple things, such as default passwords, or a failure to control administrative privileges. Companies can do lots of things to protect themselves through basic cyber hygiene.”
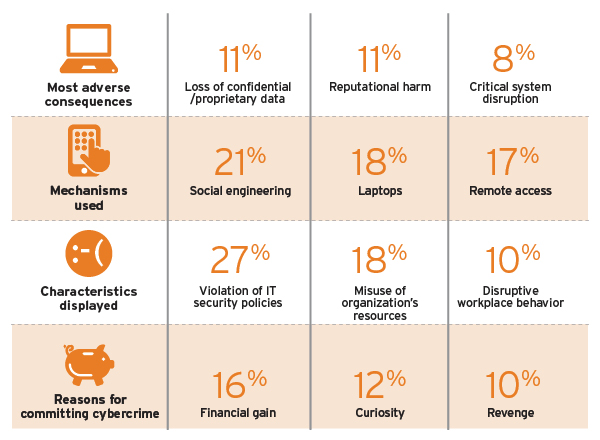
Was it an Inside Job? Survey Rates the Impact
Many insider incidents* result from employee vulnerabilities such as social engineering and loss of devices, which training can mitigate. Companies can also prevent insider incidents by monitoring employees for negative behaviors such as violation of IT policies, disruptive behavior, and poor performance reviews.
Source: PwC, U.S. State of Cybercrime Survey
So, what is a supply chain professional to do?
In recent years, a logical concept has gained traction—the “cyber supply chain.” Yes, movement of data through various connected networks does support the movement of products. But that same movable beast is an entity unto itself. A data breach of the supply chain is really a breach of the data supply chain.
Globalization and outsourcing of software and hardware brought “a process of decomposing and fragmenting the IT chain, similar to what happened to the product supply chain in the 1990s,” explains Boyson.
Now, he adds, we need “an integrated governance structure that provides control, just as you have with the product supply chain.” An early advocate of this principle, Boyson says the supply chain, risk management, C-suite, and IT positions need to collaborate.
“Senior executives and board members are increasingly being held accountable for their preparedness, as well as their response,” said attorney Judith Germano of Montclair, N.J.-based Gemano Law, at the Washington Post summit.
Some deep planning is necessary. It starts with a detailed review of your cyber supply chain. How is your data being used? Who is using it? Why is it being used? These are not supply chain-specific questions, but your answers are.
For example, can you identify all your vendors? Not knowing all your vendors is the same as not knowing who has access to your system. In fact, 10 percent of survey participants in a Business Continuity Institute study prepared for Zurich Insurance did not know all their vendors.
“Developing and implementing a master framework requires participation from leadership decision makers down to individual contributors on a warehouse floor,” says UTi’s Tomczyk.
“Carriers should assert requirements on what they need to do in order to conduct business,” he adds. “What data? With whom do they interact? How will they communicate? Who has access to what?”
Supply chain and logistics pose complex data security challenges. “Requirements can change from country to country, and from region to region,” Tomczyk says. “And, a supply chain company’s business function is to make as much data as possible visible to its customers—while preventing unauthorized access to that same information.”
Securing a Third-Party Partner
Security is a specialty unto itself. Not all IT professionals are security whizzes.
“If security falls outside the core competency of the team, do the executives partner with a qualified third party to ensure due diligence of security for their employees, customers, partners, and intellectual property/shareholders?” adds Verizon’s Ross.
“Technology subject matter experts can design systems and controls to provide risk mitigation while allowing the business to function,” says Tomczyk.
“The more critical the data, the more security layers or controls surround and protect it,” he adds. “Defense in depth is a design concept where the most critical business data or systems are structured the farthest away from ingress points, and have the most layers to penetrate.”
Battling cyber supply chain security is a never-ending story of implementation, training, modifying, and staying in touch with a fluid landscape. Here are some tips for staying on top of it:
- Keep track of personnel changes. Employees and vendors share something in common: They change. They move on, move up, or move out. Access privileges have to be modified. Someone whose role requires access to the finance system may move to a marketing role. “At that point,” says Ross, “access to the finance system needs to be revoked.”
- Monitor your trading partners’ security systems periodically. “This helps you know exactly who is logging on to your network, with what valid accounts and privileges, and through what applications at all times,” says Ross.
- Have a security protocol in place that extends to the IoT. “Distribution centers tend to stock small, valuable items in a cage controlled by card swipe, keypad, or an actual key,” says Jeffrey. The IoT lets you monitor how often that cage door opens and closes. Correlate the cage door’s openings with the number of orders picked for a specific period of time. Do you detect a significant difference?
That difference “should raise a red flag,” says Luft. “Why was the door opened? Who opened it? Did they have access and why were they in that area of the facility? If monitored consistently, the IoT makes a good security tool.”
Suppose, despite your best intentions, your supply chain data falls victim to a breach. When an intrusion warning appears, IT security people don’t panic. They spring into action like the first responders they are.
“IT security professionals have a field general mentality about any event where experience, training, and instinct take over,” says Tomczyk. “When an event occurs, they know they have the technology, processes, and people controls in place, and they can effectively respond.”
Addressing a security breach starts with identification and tactical remediation. “Close the exploit and vulnerability, and continue forward with impact assessments, analysis, and communications,” says Tomczyk.
“Make sure everyone in your company knows their roles,” adds Ross. “You might become the incident commander, and brief your corporate executives. You also might have to brief marketing, who is talking to the media.
“Have staff in certain roles report to you every 30 minutes for the first several hours of the breach until you get a handle on it,” Ross adds. “They have information coming in, and that helps you hone your guidance and direction.”
Handling Breaches Like a Boss
Consider how The UPS Store Inc. handled a security breach in 2014 when it experienced a malware intrusion at 51 locations in 24 states; about 1 percent of 4,500 franchised center locations throughout the United States.
The UPS Store responded swiftly. It hired external forensic experts to launch an investigation and eliminated the threat from the 51 center locations. The UPS Store implemented additional security enhancements, and offered identity protection and credit monitoring services at no charge for one year to any customer whose credit or debit card information may have been exposed at one of the impacted center locations.
Since the incident, The UPS Store has improved its data security initiatives to incorporate the latest technologies and industry best practices to protect customer data.
After Target’s data breach was discovered in 2013, affecting 70 million to 110 million customers, the big box chain offered one year of free credit monitoring and identity theft protection to all its U.S. shoppers. In mid-March 2015, Target received preliminary approval to settle a class action lawsuit for $10 million and a maximum (but not likely) payout of $10,000 to individual claimants, according to the New York Times.
Playing Defense
To save your company from going through this ordeal, it pays to keep the proverbial barn door closed in the first place so that no or minimal damage takes place. “A good defense beats a good offense,” says Friedman.
You and your supply chain partners need to become security fanatics. That means implementing a strong defense and using trusted third-party vendors and transportation partners. It means keeping up with compliance standards, acquiring necessary certifications, and staying alert.
The contracts you sign with vendors and carriers might state “that you have a right to audit them, to inspect how they are ensuring security, to do some form of due diligence confirming that they have security controls in place,” suggest Ross.
Increasingly, companies are turning to third-party IT security specialists. If nothing else, these relationships maintain continuity of protection while in-house IT staff move on to other roles.
We may see cyber supply chain criminals as a marauding band of genius outsiders, or chess masters gone wrong, and view the battlefield as a techno contest complete with its own arms race. But you can protect your company’s supply chain data by staying alert and planning ahead.
The Cyber Supply Chain: Assessing Your Risk
How safe is your supply chain data? A University of Maryland Robert H. Smith Business School website can help answer that question. It provides guidelines to measure and assess cyber supply chain risk based on, and part of, ongoing research, and is funded by the National Institute of Standards and Technology.
The research findings “identify cyber security framework and associated supply chain risk management’s practice guidelines,” according to Dr. Sandor Boyson, director of the Supply Chain Management Center, and research professor at the Robert H. Smith School of Business.
“Users take a series of assessments,” explains Boyson. “The site helps analyze IT systems, supply chain systems, and insurability systems. It also offers an executive dashboard that explains the results and how they compare with other companies.”
It takes 30 to 40 minutes to complete each assessment. Because the assessments are interdisciplinary, it helps to have members of the IT, supply chain, and risk management departments available to help answer questions. The insurance assessment section might be of particular interest to publicly traded companies.
To take the completely anonymized assessment go to: https://cyberchain.rhsmith.umd.edu.
DO’s and DON’Ts of Cyber Security
Computer security awareness is not just for your IT department; it’s for everyone. Here are a few do’s and don’ts.
- Think before you click. Sometimes scamming messages can look legit. But there are a few tests you can do before you open it. “Hover your mouse over the top of the URL,” says Brian Posey, TechRepublic. “You’ll see the true hyperlinked address, which should be the same as the displayed address. Also beware of misspelled domain names, requests for personal information, or anything that just doesn’t look right. It probably isn’t.”
- Keep your office computer locked whenever you step away. Phones and laptops get lost or stolen; so keep them locked. They tend to hold sensitive company information such as emails, texts, files, etc. (Translation: I trust you but I don’t trust the person who entered your cubicle when you went to the restroom or the one sitting next to you in Starbucks.)
- Don’t use apps without IT’s knowledge, approval, and support. The shadow app might be a Trojan horse of another color. Use your computer for work. Don’t browse sites.
- Inform your designated security contact. If you suspect your company is being targeted, or your computer is acting up—running too slow, displaying strange error messages, or having an unusual response to keystrokes—report it.