Articles
Security

Three Ways to Mitigate Insider Risk in Your Supply Chain
“Insider threat” has long been a familiar security topic for C-suite executives in every industry. In fact, 90% of organizations feel vulnerable to insider attacks, according to IBM. Yet, when creating risk mitigation programs for insider threats, many organizations overlook their nonemployees—the people who work for their third-party vendors, partners, and contractors.
Read More
What’s Lurking in Your Supply Chain?
You may think your company is well protected when it comes to cybersecurity, but an often overlooked source of vulnerability is your supply chain. If you can’t honestly say you are fully apprised of the security postures of your vendors, partners, and contractors, then you are already at major risk of a cyberattack.
Read More
3 Big Barriers to IIoT Integration
From monitoring air quality in "smart cities" like Chicago and New York City to tracking health data in real time on smart watches, the Internet of Things (IoT) is everywhere. IoT applications look promising for the manufacturing industry as well: European aircraft manufacturer Airbus is developing Industrial Internet of Things (IIoT) technologies to provide valuable […]
Read More
Stop, Thief! Five Ways to Protect Your Supply Chain
Today’s supply chain ecosystem is increasingly complicated. We rely on suppliers and buyers across the globe and use multiple transport modes, languages, currencies, and laws across borders.
Read MoreGoing the Distance: Securing Supply Chains From Cyber Attack
All over the world, business are achieving their goals with more ease than ever before, thanks to digital disruption. Ambitions that would have taken decades to achieve in the past can now be attained in significantly less time, whether you are expanding globally, automating low-level tasks or scaling up. But this digital awakening has also […]
Read More
Eight Ways to Minimize Supply Chain Risk
Supply chain attacks aren’t anything new, but threat actors continue to find new ways to breach networks. The 2013 Target breach and more recent NotPetya, Trisis, and Wipro compromises serve as not-so-gentle reminders that supply chain attacks are damaging and costly and present many risks to both businesses and their suppliers.
Read More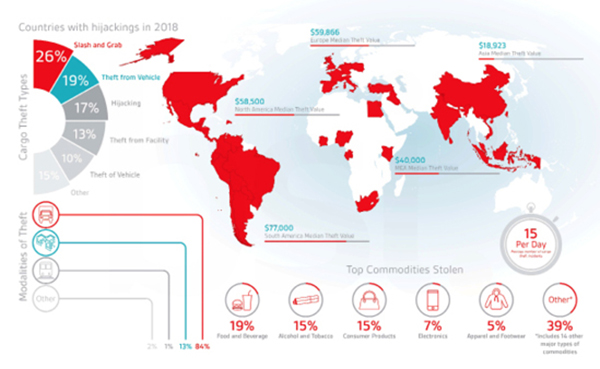
Stop, Thief!
TT Club and BSI have issued the second edition of their report on global cargo theft, the first to cover a full year. The report analyzes cargo theft by modality, theft type (modus operandi), commodities targeted, and the value of losses across the major regions of the world (see chart above). Among the notable findings: […]
Read More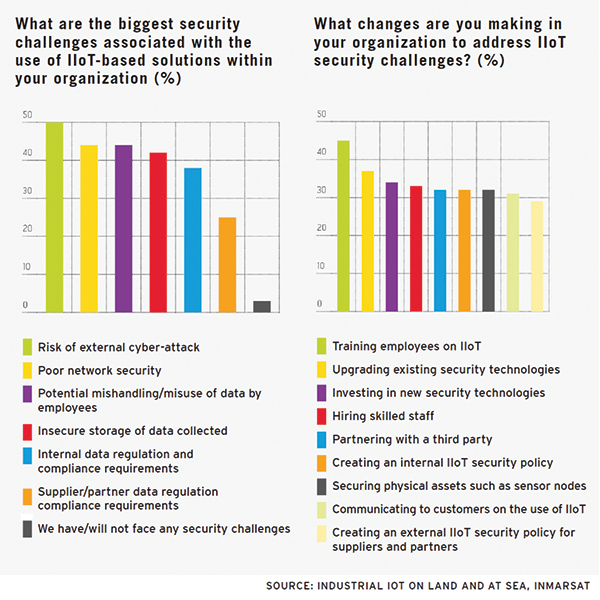
Is Your IoT Deployment Secure?
Transportation and logistics companies recognize they must strengthen their approaches to cybersecurity but are not yet taking the practical steps to safeguard their industrial Internet of Things (IoT) deployments, according to a study done on behalf of Inmarsat. According to the study, which surveyed 125 businesses across the transport industry, 64% of respondents say their […]
Read More
The ABCs of Supply Chain Cybersecurity
Supply chain cybersecurity is one of the biggest issues facing logistics planners.
Read MoreDefending Against Supply Chain Hackers
While your company may have excellent cyber security practices in place, your suppliers may not. These best practices will help protect your company from hackers who attack your supply chain partners. 1. Review Incident Response Plans. Always make sure vendors have an incident response plan in place before conducting business with them. If there is […]
Read More